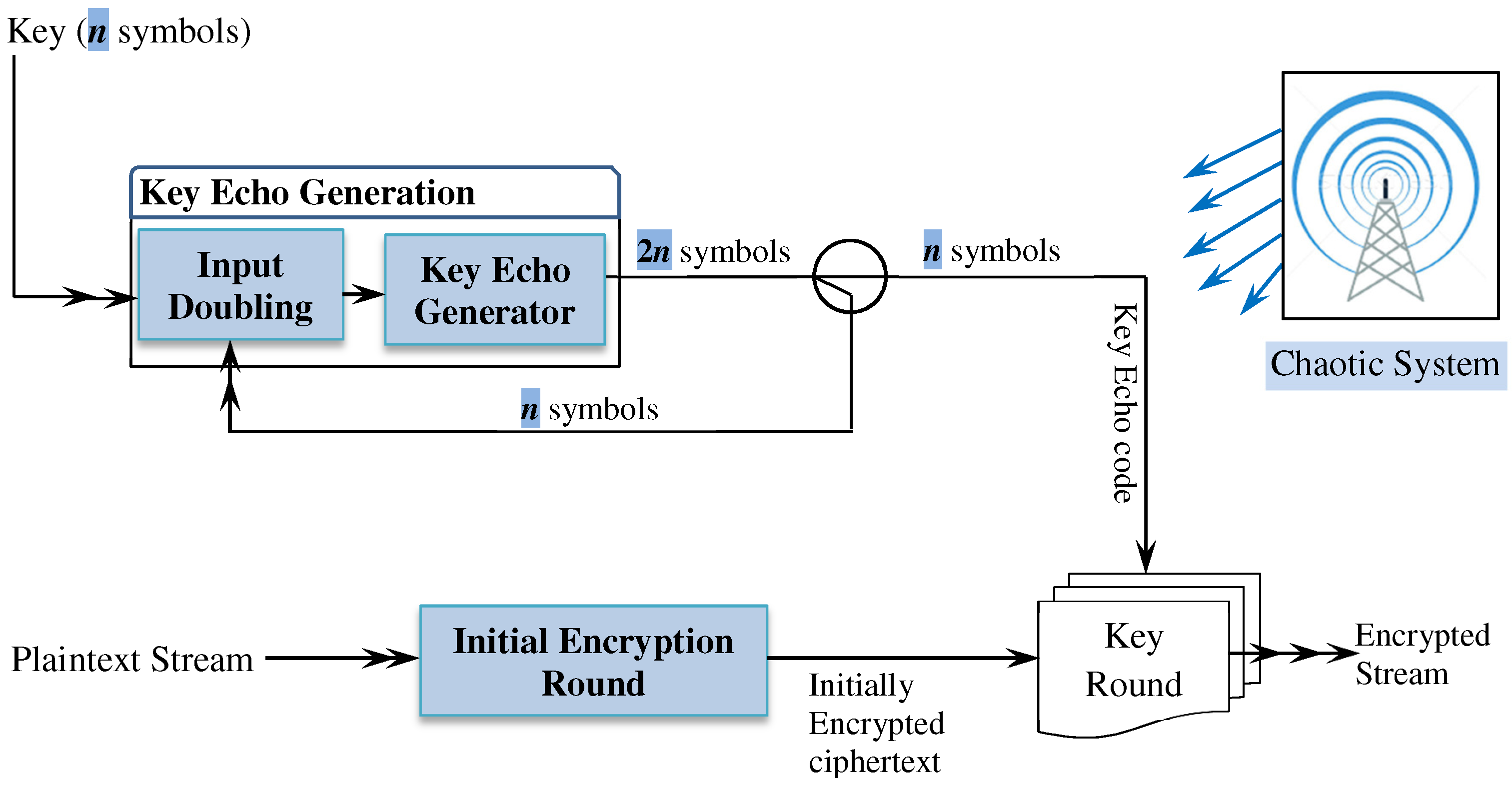
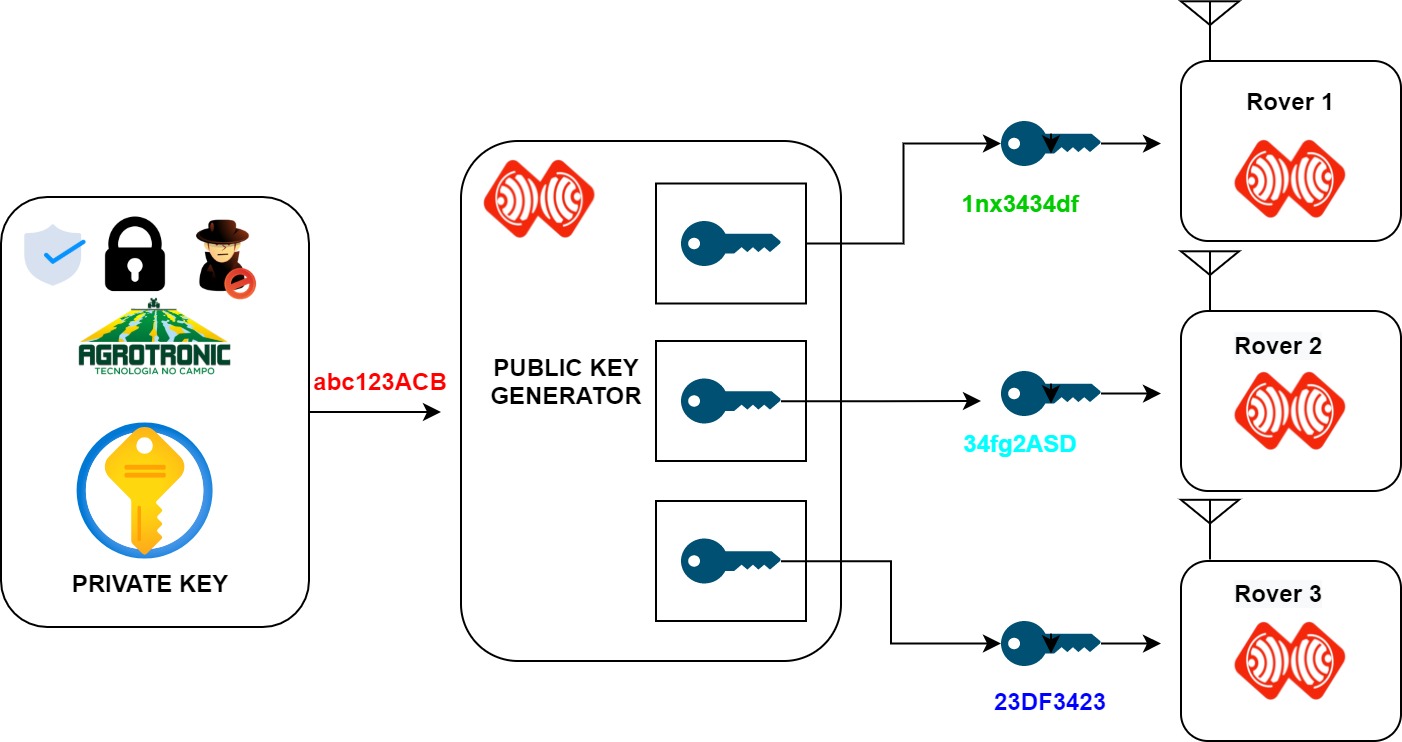
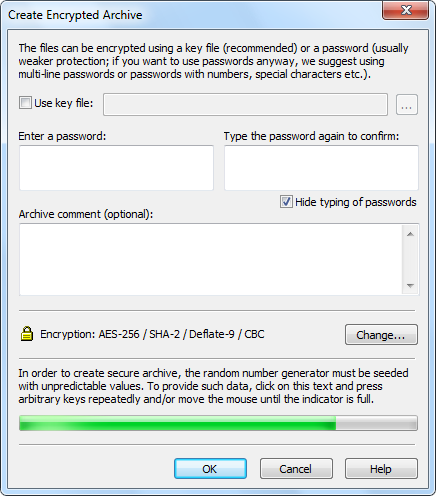
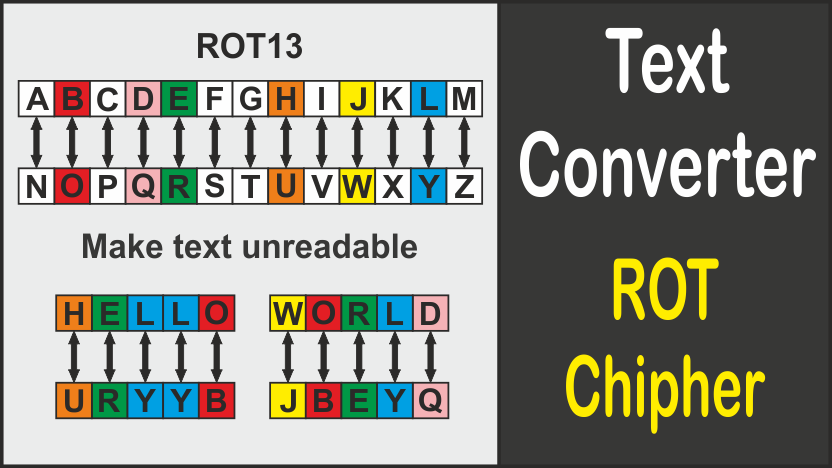
Example of an embedded encryption scheme: real time image encryption... | Download Scientific Diagram

Enhanced key-generation algorithm using MRMCTT in Data encryption standard algorithm | Semantic Scholar
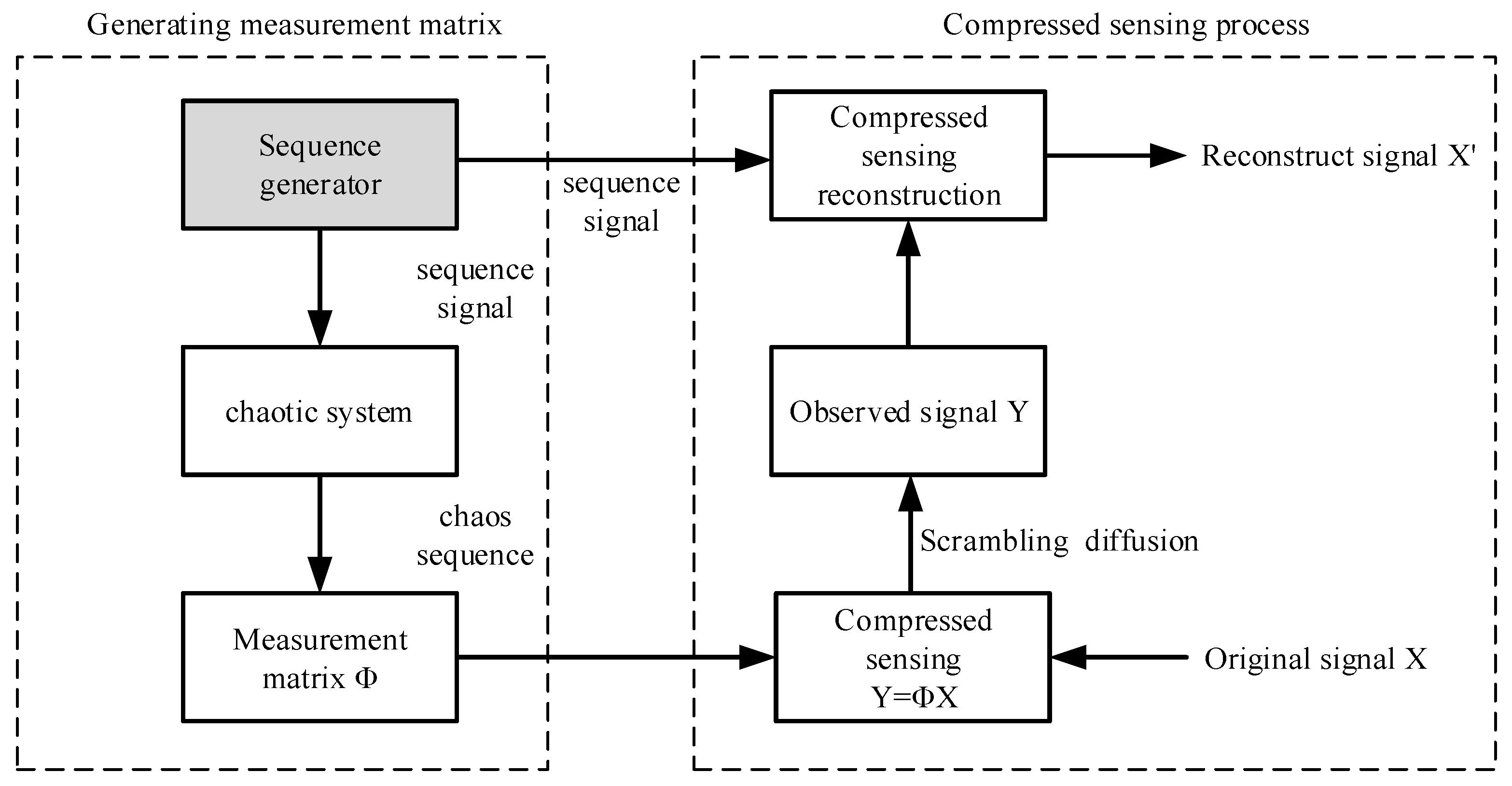
Entropy | Free Full-Text | Image Parallel Encryption Technology Based on Sequence Generator and Chaotic Measurement Matrix

CJMCU 608 Cryptographic Key Storage Random Number Generator Signature Encryption Decryption Module|encryption keys| - AliExpress
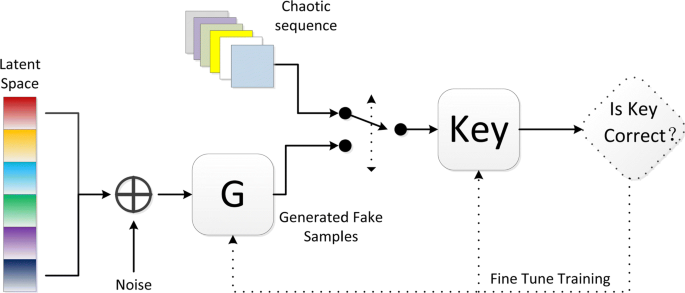
A novel image encryption algorithm based on least squares generative adversarial network random number generator | SpringerLink

Password Generator | Encrypting and Decrypting Password with Symmetric Encryption using Python - YouTube
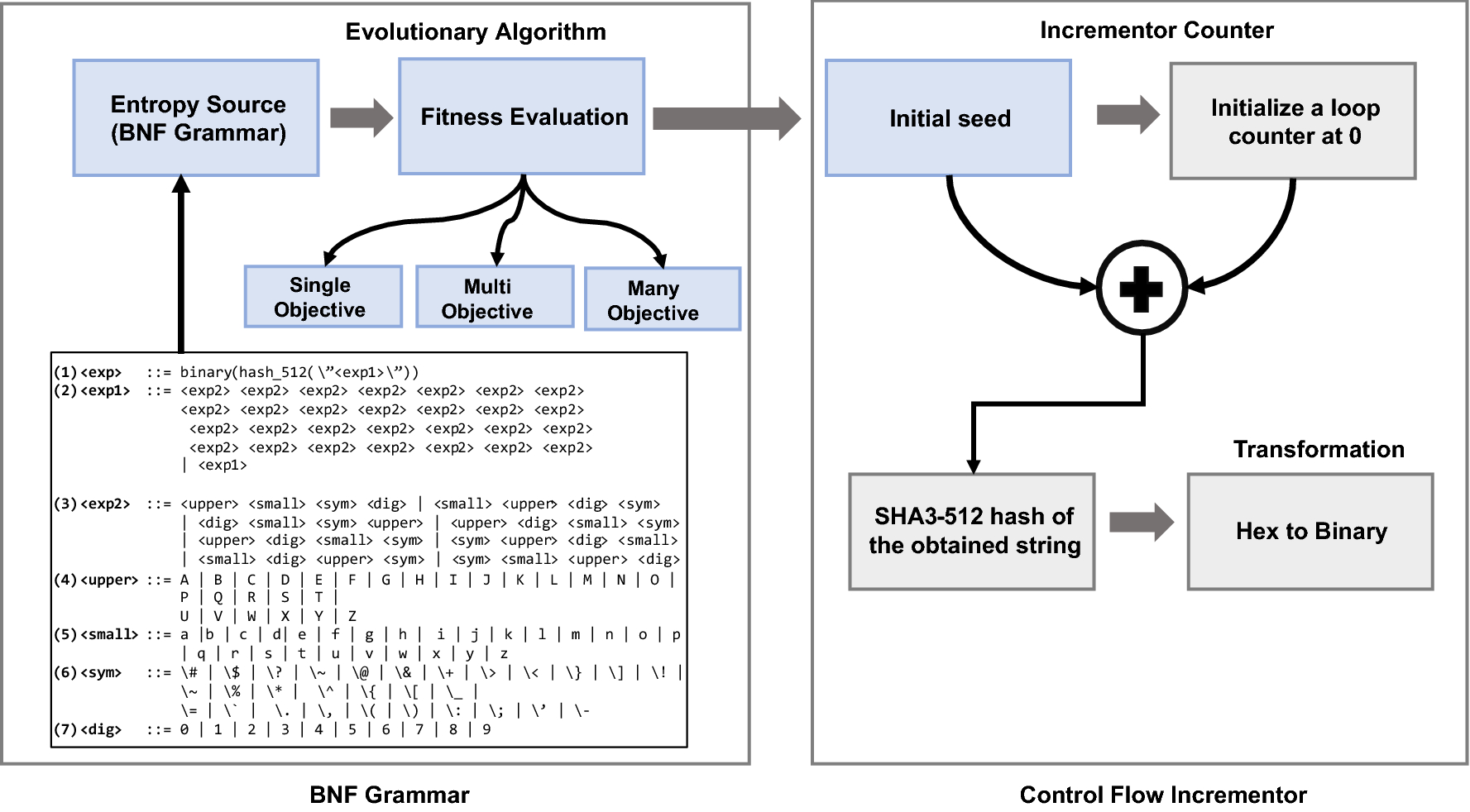
Design of a cryptographically secure pseudo random number generator with grammatical evolution | Scientific Reports