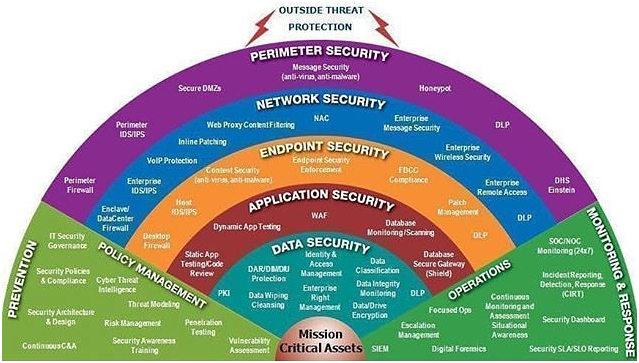
New York Cybersecurity Requirements for Financial Services Companies (NY-CRFSC) | by Golden Data Law | Golden Data | Medium
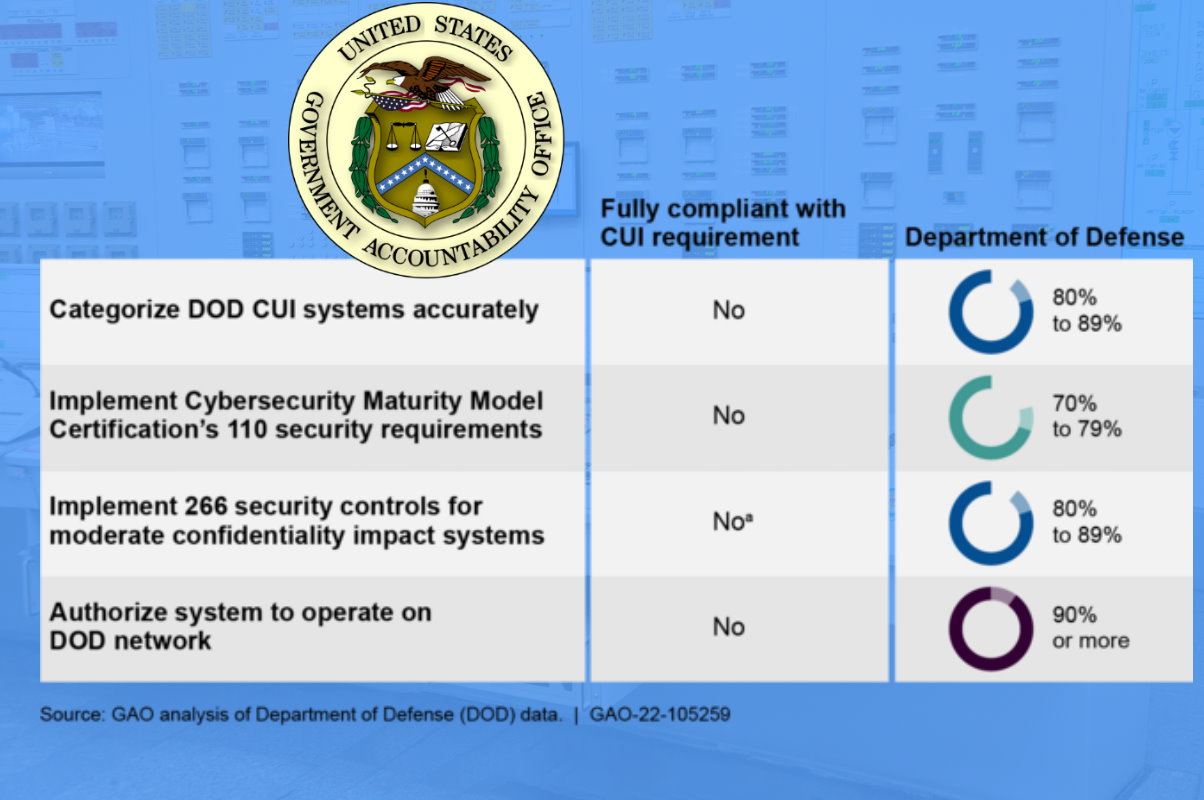
US GAO reports that DOD has partially implemented selected cybersecurity requirements for CUI systems - Industrial Cyber
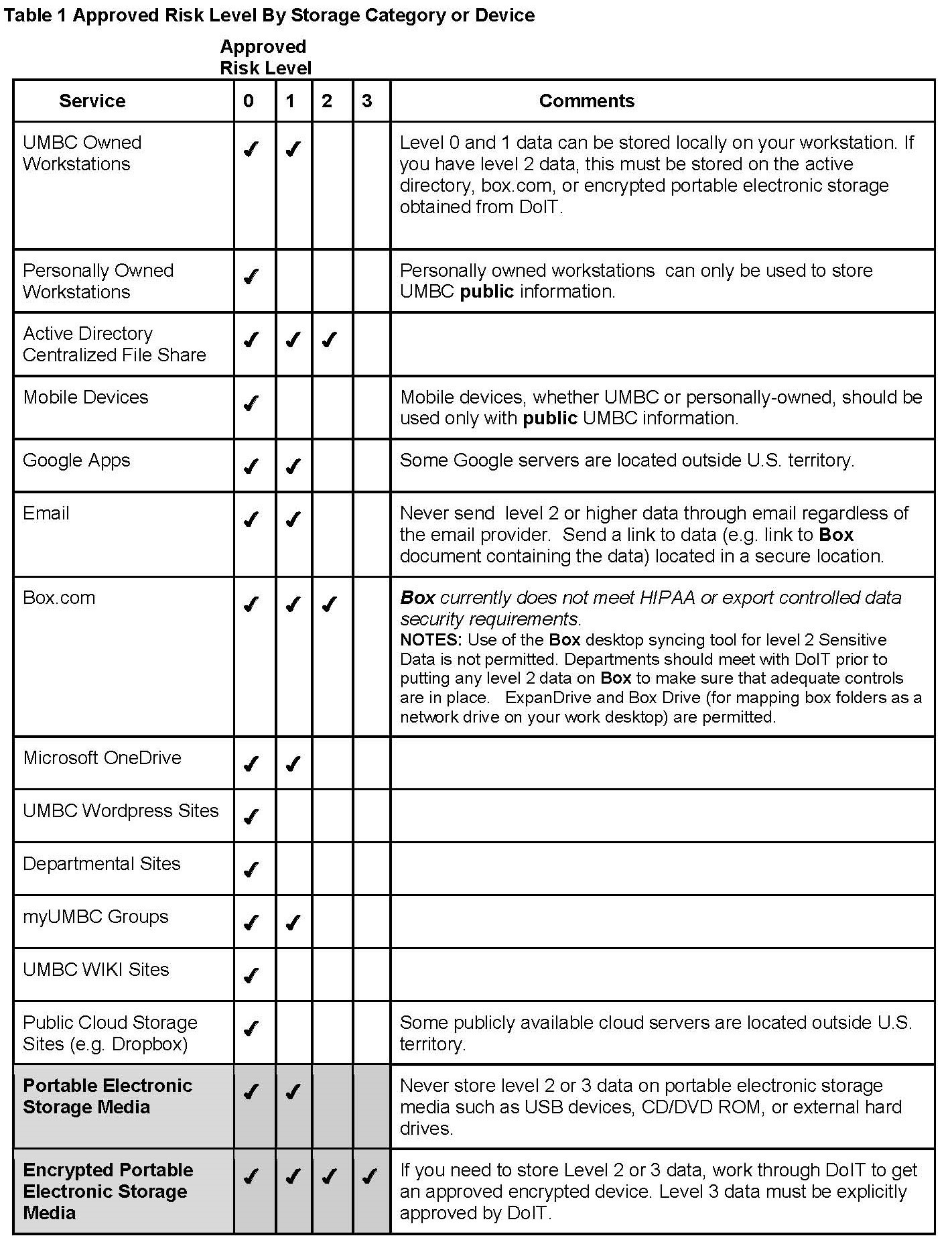


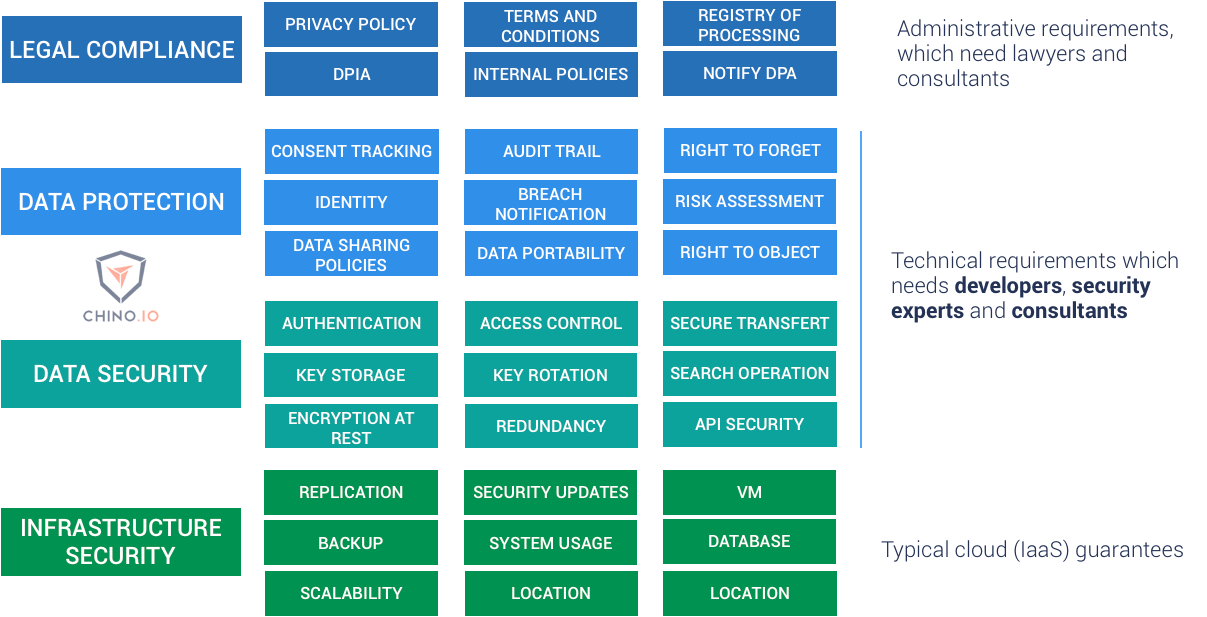











![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2020/08/visual-representation-of-data-privacy-and-data-security-areas.png)